“We’re not just fighting an epidemic; we’re fighting an infodemic,” said Tedros Adhanom Ghebreyesus, Director-General of the World Health Organization (WHO) during a gathering of foreign policy and security experts in Munich, Germany, in February, referring to fake news and opportunistic cyber attacks that “spreads faster and more easily than this virus,” he said. COVID-19, and various measures used to control the spread of the virus, has fundamentally changed the cybersecurity landscape. Remote work is suddenly the new normal, with many companies forced to develop the infrastructure to make that possible in the early days and weeks of the outbreak. Remote work already made companies more vulnerable by providing access to sensitive information over unsecured networks but in the rush to create a decentralized infrastructure an extensive and largely unsecured edge has been exposed. “Traditional cybersecurity controls dictate a centralized approach where data is consolidated from different sources to perform analysis and investigation. With swift […]
Most Popular Articles

MRI Software: Exploring the 2025 IPO & Sale Options
This Research Note examines a report from Reuters that MRI Software is to be listed in an IPO or sold. We explore the development of the business over the last 10 years, since it was acquired by private equity owners, highlight their software acquisitions for commercial real estate applications addressing integrated workplace management, tenant experience […]

Podcast 40: Stiles Property Management Found $400K+ in Hidden Savings
Most property managers know their buildings are hemorrhaging money through inefficient systems. The problem? They have no idea where to start looking. Devon Newton, VP of Property Management at Stiles, faced this exact challenge with 110 East, a new Class A development in Charlotte’s Southpark district. Despite managing 116 properties across the Southeast, she found […]
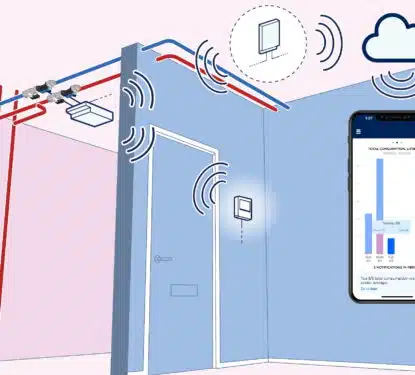
Smartvatten Strengthens European Position with 2025 LeakLook Acquisition
This Research Note examines Smartvatten, a Finnish specialist in water efficiency technology and expertise in Northern Europe. It updates our previous article in March 2024, covering Smartvatten’s solutions, key developments in 2024, sustainability partnerships and the September 2025 acquisition of LeakLook, a Finnish specialist in IoT-driven water monitoring for real estate. Smartvatten Profile Established in […]
