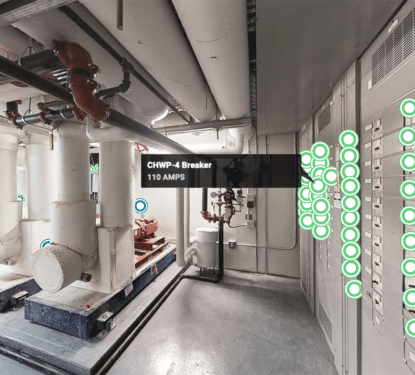
How can cyber security teams secure a smart building without first knowing what devices, systems, and connections are active in the building? That is the quandary facing building owners and managers as smart devices proliferate across their facilities, leaving a large and growing attack surface undefended. Those responsible for cyber security have to map entire networks in order to identify and address vulnerabilities, but it is not that easy with the real-world complexities of buildings and a wide range of important security issues are falling through the gaps.
“To conduct a comprehensive cyber risk evaluation of all of the devices on a particular network, a complete audit of all of the device and systems connections is necessary,” reads our latest cyber research. “Unfortunately, however, the automated network scanning tools and technologies that are commonly deployed in IT environments to facilitate this audit process are ill-suited to OT environments. As smart building OT devices and systems often run on outdated legacy protocols they are not designed to respond to the kinds of messaging protocols used by IT scanning processes that report back on the device status, firmware and so on.”
Indeed, such scanning approaches can even be damaging for operational technology (OT) devices and systems. A traditional scan of an OT network generally doesn’t work as many OT devices will “brick” during the scan —meaning, that due to a patch or an upgrade a device is essentially corrupted and made useless, from a connectivity or cyber security perspective. Such scenarios can lead to significant cost and disruption for building owners.
Intelligent Buildings cite a case where 60% of the 1,000+ devices running at an NYC-based building were knocked offline due to the use of an IT vulnerability detection tool without prior testing, the scan itself resulted in estimated damages of $1.25 million. The building owner then required engagement from contractors to manually restart their failed devices. Systems were eventually restored and re-verified after a full 15 days offline.
“For OT networks, therefore, more passive network scanning approaches are more advisable, whereby instead of actively polling for devices on a network, a scanner instead listens out for messages from systems and devices on the network and uses AI/Machine Learning techniques to evaluate based on the messaging protocols used by devices and the structure of the messages sent to determine what OT devices reside on the network,” reads our new cyber report.
“This process does have its limitations however, as some OT devices can lie dormant for long periods, meaning scans may need to be carried out over long periods to ensure that all device connections are properly documented,” our comprehensive research explains. “In some cases, expensive and time-consuming manual inspection may also be required to supplement a passive scanning approach, with security specialists literally walking around the building to record all of the physical device connections to a particular network.”
OT systems are often not the primary target for attacks, but remain subject to a large and growing volume of cyber-attacks as OT gets more connected and hackers get more building savvy. The vulnerabilities of building systems and consumer-grade IoT devices that are widely distributed through buildings are now well established. With the continued presence of large volumes of unprotected or poorly configured devices and systems openly searchable on the Internet, it seems only a matter of time before we see growing waves of cyber attacks utilizing this growing OT vulnerability in smart buildings.
“The building technology industry was not founded on a strong security model. The early products were designed to automate mechanical functions for building engineers. The products were designed to be easy to use, and security wasn’t an early consideration,” says Charles Meyers, SVP & Chief Technical Architect at Wells Fargo. “I found myself emphasizing, again and again, the fact that this industry needed to change if we wanted to see more secure products and services in the future. Our goal is to get the disparate motivations in the supply chain better aligned, as everyone will have a role in improving security."