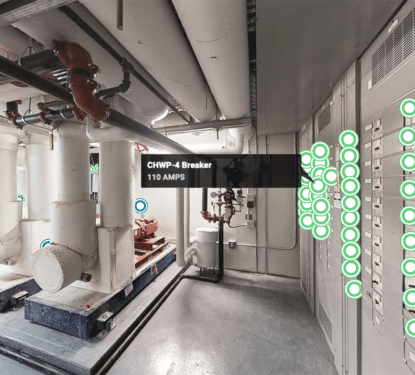
A damning IoT security breach occurred this week as a hacker group gained access to video surveillance feeds, as well as company and customer data, of Silicon Valley security startup Verkada. The hackers gained access to over 150,000 cameras, including those in Tesla factories and warehouses, Cloudflare offices, Equinox gyms, hospitals, jails, schools, police stations, and Verkada’s own offices. This hack not only exposed the company and its customers but also highlighted the pervasive nature of video surveillance and the vulnerability of such devices, undermining the growth of the IoT trend across the world.
Calling it a “hack” might be a little misleading, suggesting some kind of complex technical process was involved to gain access to the sensitive data. In fact, the methods used by the attackers were entirely unsophisticated. The group gained access to the Verkada system through a “Super Admin” account, via username and password credentials they found for an administrator account publicly exposed on the internet. With that publicly available information the group was able to gain access to all customers’ camera feeds and video archives, as well as sensitive customer data and confidential company information on Verkada itself.
“We found super admin credentials in a python script on a publicly exposed Veracode Jenkins Plugin on the Verkada server, which allowed us to log in to their web app with super admin privileges,” Tillie Kottmann, a member of the hacker collective, explained. “We did not exploit any flaws or vulnerabilities. The cameras have a built-in maintenance backdoor, which allows anyone with super admin privileges to access a root shell on any camera of any customer at the click of a button.”
Kottmann said their group was able to obtain root access to the cameras, meaning they could use the cameras to execute their own code. That access could, in some instances, allow them to pivot and obtain access to the broader corporate network of Verkada’s customers, or hijack the cameras and use them as a platform to launch future hacks. Hackers were even able to see a detailed record of who used Verkada access control cards to open certain doors, with specific dates and times. Obtaining this degree of access to the camera didn’t require any additional hacking, as it was a built-in feature, Kottmann said.
“The hack exposes just how broadly we’re being surveilled, and how little care is put into at least securing the platforms used to do so, pursuing nothing but profit. It’s just wild how I can just see the things we always knew are happening, but we never got to see,” said Kottmann, who added their reasons for hacking are “lots of curiosity, fighting for freedom of information and against intellectual property, a huge dose of anti-capitalism, a hint of anarchism -- and it’s also just too much fun not to do it.”
Beyond the hack, the breach exposes the fact that Verkada administrators have broad and easy access to customer video feeds, even in sensitive environments such as schools, hospitals, women’s health clinics, police stations, and jails. This is even more concerning for customers of a company that was embroiled in an internal sexual harassment scandal on their own employees just last October. Then, a group of male sales managers used Verkada cameras in their own offices to take photos of female colleagues, which were then posted in a private Slack channel alongside sexually explicit jokes.
“If you are a company who has purchased this network of cameras and you are putting them in sensitive places, you may not have the expectation that in addition to being watched by your security team that there is some admin at the camera company who is also watching,” said Eva Galperin, director of cybersecurity at the Electronic Frontier Foundation. “There are many legitimate reasons to have surveillance inside of a company. The most important part is to have the informed consent of your employees. Usually, this is done inside the employee handbook, which no one reads.”
Verkada, founded in 2016, sells cameras that customers can access and manage through the web. Their client list includes 30 Fortune 500 companies, such as Tesla and Cloudflare, as well as hundreds of major facilities including Halifax Health, a Florida hospital; Sandy Hook Elementary School in Connecticut; Madison County Jail in Alabama; and Wadley Regional Medical Center in Texas. In January 2020, the company raised $80 million in venture capital funding, valuing the company at $1.6 billion. Among the investors was Sequoia Capital, one of Silicon Valley’s oldest firms, who will no doubt be reconsidering their involvement.
The company has been hiring at an unprecedented rate in recent years according to statistics available on LinkedIn. The data also indicating that Verkada may have prioritized sales expansion over developing their engineering team. This breach, and others, underlines the worrying trend of cyber security negligence among IoT-related Startup companies, dealing a real blow for the IoT as a whole.
As the dust settles on another scandal involving easily breachable IoT systems, the same old questions are likely to arise. Are we rushing into this connected world? Is there enough control over the security of these systems? And even, is the IoT broken and fit for purpose? The answers to these questions will have a direct impact on market growth and the technological development of society as a whole. Verkada sales will no doubt suffer from this incident but is it enough to allow the market to retrospectively enforce change or should we have better governance of the IoT? And, how many more major incidents do we need to make real changes to safeguard society against this uncontrolled technological development?